TISH: Trustworthy Information Systems for Healthcare (2009-2018)
This project is no longer active; this page is no longer updated.
Related projects:
[Amanuensis],
[Amulet],
[Auracle],
[SIMBA],
[THaW]
Related keywords:
[authentication],
[iot],
[mhealth],
[patent],
[privacy],
[security],
[sensors],
[survey],
[wearable],
[wifi]
Summary
In the TISH (Trustworthy Information Systems for Healthcare)
project we explored wearable and portable devices for use in health
monitoring and management, with an emphasis on the security and
privacy issues that arise with these devices and their apps. We
considered wearable, mobile, or home-based technologies being used by
patients or clinical staff, and addressed issues of person
identification and authentication, privacy and data sharing, secure
data processing, anonymity in wireless-network communications, and
mobile sensing. Some of this work is summarized below.
Much of this work culminated in the
THaW project
and inspired work in the
Amanuensis,
Amulet,
Auracle, and
SIMBA projects.
This page also includes work funded in the SHARPS and PC3 grants.
Overview, challenges, surveys:
Early in this project we wrote an extensive survey of the literature
regarding privacy in mHealth technology
[avancha:survey],
and extracted a threat model from that work
[kotz:mhealth-threats,
kotz:mhealth-spimacs].
Later in the project we held a workshop to review the state of the science
[anthony:sith3].
A 2012 presentation at Microsoft Research gave an overview of several
of the research activities noted on this page; see the
[video].
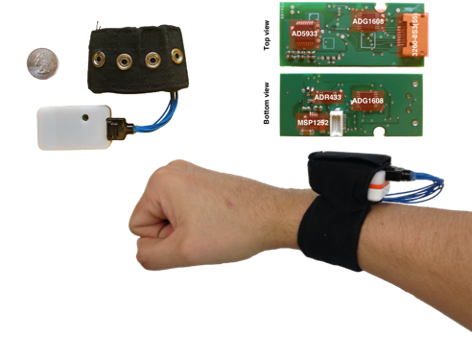 Biometric identification/verification.
In this work we address two critical challenges. First, we evaluate
the use of bioimpedance for recognizing who is wearing
wireless sensors and show that bioimpedance is a feasible
biometric. Second, we investigate the use of accelerometers for
verifying whether two of these wireless sensors are on the same
person and show that our method is successful as distinguishing
between sensors on the same body and on different bodies. We stress
that any solution to these problems must be usable, meaning the user
should not have to do anything but attach the sensor to their body
and have them just work. This work is best described in Cornelius'
PhD thesis
[cornelius:thesis],
and also appeared in several papers
[cornelius:wearable,
cornelius:impedance,
cornelius:j-same-body,
cornelius:same-body,
cornelius:biometrics-poster].
We also conducted an early investigation into the prospect of
identifying people with their 'vocal resonance', that is, the sound of
their voice as recorded through their body
[cornelius:voice-tr];
this work later was finished under the
THaW project.
Biometric identification/verification.
In this work we address two critical challenges. First, we evaluate
the use of bioimpedance for recognizing who is wearing
wireless sensors and show that bioimpedance is a feasible
biometric. Second, we investigate the use of accelerometers for
verifying whether two of these wireless sensors are on the same
person and show that our method is successful as distinguishing
between sensors on the same body and on different bodies. We stress
that any solution to these problems must be usable, meaning the user
should not have to do anything but attach the sensor to their body
and have them just work. This work is best described in Cornelius'
PhD thesis
[cornelius:thesis],
and also appeared in several papers
[cornelius:wearable,
cornelius:impedance,
cornelius:j-same-body,
cornelius:same-body,
cornelius:biometrics-poster].
We also conducted an early investigation into the prospect of
identifying people with their 'vocal resonance', that is, the sound of
their voice as recorded through their body
[cornelius:voice-tr];
this work later was finished under the
THaW project.
Authentication of computer users:
We invented the concept of bilateral authentication and
applied it to the challenge of continuous authentication of
desktop computer users. Common authentication methods based on
passwords, tokens, or fingerprints perform one-time authentication
and rely on users to log out from the computer terminal when they
leave. One solution is to authenticate users continuously while they
are using the terminal and automatically log them out when they
leave. In our solution, explored fully in Mare's dissertation
[mare:thesis]
and the papers below, a user wears a bracelet (with a built-in
accelerometer, gyroscope, and radio) on her dominant wrist. When the
user interacts with a computer terminal, the bracelet records the
wrist movement, processes it, and sends it to the terminal. The
terminal compares the wrist movement with the inputs it receives
from the user (via keyboard and mouse), and confirms the continued
presence of the user only if they correlate. Because the bracelet is
on the same hand that provides inputs to the terminal, the
accelerometer and gyroscope data and input events received by the
terminal should correlate because their source is the same -- the
user's hand movement. Our approach performed continuous
authentication with 85% accuracy in verifying the correct user and
identified all adversaries within 11 seconds. For a different
threshold that trades security for usability, it correctly verified
90% of users and identified all adversaries within 50 seconds
[mare:thesis,
mare:patent9832206,
mare:zebra-tr,
mare:zebra14].
This project was renamed CSAW and was completed under the
THaW project.
Privacy and data sharing:
We explored several questions related to the willingness of people to
share mHealth data, the means to attest to its provenance, and
privacy-preserving systems to retrospectively detect when people were
in spatio-temporal proximity. In Prasad's dissertation
[prasad:thesis]
and related papers we present our findings about factors that affect
people's sharing behavior, describe scenarios in which people may
wish to collect and share their personal health-related information
with others, but may be hesitant to disclose the information if
necessary controls are not available to protect their privacy, and
propose frameworks to provide the desired privacy controls. We
introduce the concept of close encounters that allow users to
share data with other people who may have been in spatio-temporal
proximity. We developed two smartphone-based systems that leverage
stationary sensors and beacons to determine whether users are in
spatio-temporal proximity. The first system, ENACT, allows patients
diagnosed with a contagious airborne disease to alert others
retrospectively about their possible exposure to airborne virus. The
second system, SPICE, allows users to collect sensor information,
retrospectively, from others with whom they shared a close
encounter. We present design and implementation of the two systems,
analyse their security and privacy guarantees, and evaluate the
systems on various performance metrics. Finally, we evaluate how
Bluetooth beacons and Wi-Fi access points can be used in support of
these systems for close encounters, and present our experiences and
findings from a deployment study on Dartmouth campus.
[prasad:thesis,
prasad:nethealth13,
prasad:provenance-poster,
prasad:bfitbit,
prasad:fitbit,
prasad:msthesis].
Hide-n-Sense: wireless security and anonymity.
Although some work on mHealth sensing addressed security,
achieving strong privacy for low-power sensors remains a
challenge. We make three contributions. First, we propose an mHealth
sensing protocol that provides strong security and privacy
properties at the link layer, with low energy overhead, suitable for
low-power sensors. The protocol uses three novel techniques:
adaptive security, to dynamically modify transmission overhead; MAC
striping, to make forgery difficult even for small-sized Message
Authentication Codes; and asymmetric resource requirements, in
recognition of the limited resources in tiny mHealth
sensors. Second, we demonstrate its feasibility by implementing a
prototype on a Chronos wrist device, and evaluating it
experimentally. Third, we provide a security, privacy, and energy
analysis of our system
[mare:hns-j,
mare:hns-w,
mare:hns-tr].
Plug-n-Trust: secure sensing and data processing.
Plug-n-Trust (PnT) was a novel approach to protecting both the
confidentiality and integrity of safety-critical medical sensing and
data processing on vulnerable mobile phones. With PnT, a plug-in
smart card provides a trusted computing environment, keeping data
safe even on a compromised mobile phone. By design, PnT is simple to
use and deploy, while providing a flexible programming interface
amenable to a wide range of applications. We designed an
implementation for Java-based smart cards and Android phones, in
which we use a split-computation model with a novel path hashing
technique to verify proper behavior without exposing confidential
data. Our experimental evaluation demonstrates that PnT achieves its
security goals while incurring acceptable overhead
[sorber:pnt,
sorber:pnt-poster].
Sensing blood-pressure reliably:
We built a user-friendly, mobile health-data collection system
designed to support minimally trained, non-clinical health workers to
gather data about blood pressure and body weight using off-the-shelf
medical sensors. This system comprises a blood-pressure cuff, a
weighing scale and a portable point-of-sales printer. With this
system, we introduced a new method to record contextual information
associated with a blood-pressure reading using a tablet's touchscreen
and accelerometer. This contextual information can be used to verify
that a patient's lower arm remained well-supported and stationary
during her blood-pressure measurement. The work resulted in Murthy's
MS thesis and Smithayer's BA thesis
[murthy:thesis,
murthy:bp,
smithayer:bp].
People
Many people were involved in TISH projects; those involved as
co-authors include
Denise Anthony,
Sasikanth Avancha,
Amit Baxi,
Andrew Campbell,
Cory Cornelius,
Andrew Gettinger,
Carl A. Gunter,
Ryan Halter,
M. Eric Johnson,
Shloka R. Kini,
David Kotz,
Shrirang Mare,
Zachary Marois,
Lisa Marsch,
Andrés Molina-Markham,
Rima Narayana Murthy,
Kolin Paul,
Ronald Peterson,
Aarathi Prasad,
Minho Shin,
Joseph Skinner,
Sean Smith,
Emma N. Smithayer,
Jacob Sorber,
and
Timothy Stablein.
Funding
TISH research was primarily funded by
the NSF Trustworthy Computing program
(Award 0910842),
but we also had related funding
from the NSF IIS program
(Award 1016823),
from the NSF Computer and Network Systems program (PC3)
(Award 1143548),
from HHS-ONC through the SHARP program (see SHARPS website),
the Department of Homeland Security (DHS-NCSD) through
ISTS,
and
from the Intel University Research Council.
The views and conclusions contained on this site and in its documents
are those of the authors and should not be interpreted as necessarily
representing the official position or policies, either expressed or
implied, of the sponsor(s). Any mention of specific companies or
products does not imply any endorsement by the authors or by the
sponsor(s).
Papers (tagged 'tish')
[Also available in BibTeX]
Papers are listed in reverse-chronological order.
Follow updates with RSS.

- 2017:
- 2016:
- 2014:
-
Aarathi Prasad, Jacob Sorber, Timothy Stablein, Denise Anthony, and David Kotz.
Understanding User Privacy Preferences for mHealth Data Sharing.
MHealth: Multidisciplinary Verticals, chapter 30, pages 545–570.
Edited by Sasan Adibi.
Taylor & Francis (CRC Press), November 2014.
doi:10.1201/b17724-34.
ISBN13: 978-1-4822-1480-2.
[Details]
-
Rima Narayana Murthy.
mCollector: Sensor-enabled health-data collection system for rural areas in the developing world.
Master's thesis, Dartmouth College Computer Science, Hanover, NH, August 2014.
Available as Dartmouth Technical Report TR2015-788.
[Details]
-
Cory Cornelius, Ronald Peterson, Joseph Skinner, Ryan Halter, and David Kotz.
A wearable system that knows who wears it.
Proceedings of the International Conference on Mobile Systems, Applications, and Services (MobiSys), pages 55–67.
ACM, June 2014.
doi:10.1145/2594368.2594369.
[Details]
-
Shrirang Mare, Jacob Sorber, Minho Shin, Cory Cornelius, and David Kotz.
Hide-n-Sense: preserving privacy efficiently in wireless mHealth.
Mobile Networks and Applications (MONET), volume 19, number 3, pages 331–344.
Springer-Verlag, June 2014.
doi:10.1007/s11036-013-0447-x.
Special issue on Wireless Technology for Pervasive Healthcare.
[Details]
-
Shrirang Mare, Andrés Molina-Markham, Cory Cornelius, Ronald Peterson, and David Kotz.
ZEBRA: Zero-Effort Bilateral Recurring Authentication (Companion report).
Technical Report number TR2014-748, Dartmouth Computer Science, May 2014.
This project has been renamed CSAW.
[Details]
-
Shrirang Mare, Andrés Molina-Markham, Cory Cornelius, Ronald Peterson, and David Kotz.
ZEBRA: Zero-Effort Bilateral Recurring Authentication.
Proceedings of the IEEE Symposium on Security & Privacy, pages 705–720.
IEEE, May 2014.
doi:10.1109/SP.2014.51.
This project has been renamed CSAW.
[Details]
-
Cory Cornelius, Zachary Marois, Jacob Sorber, Ron Peterson, Shrirang Mare, and David Kotz.
Vocal resonance as a biometric for pervasive wearable devices.
Technical Report number TR2014-747, Dartmouth Computer Science, February 2014.
[Details]
-
Rima Murthy and David Kotz.
Assessing blood-pressure measurement in tablet-based mHealth apps.
Proceedings of the Workshop on Networked Healthcare Technology (NetHealth), pages 1–5.
IEEE, January 2014.
doi:10.1109/COMSNETS.2014.6734920.
[Details]
- 2013:
-
Denise Anthony, Andrew Campbell, Thomas Candon, Andrew Gettinger, Carl A. Gunter, M. Eric Johnson, David Kotz, Lisa Marsch, Andrés Molina-Markham, Karen Page, and Sean Smith.
Securing Information Technology in Healthcare.
IEEE Security & Privacy, volume 11, number 6, pages 25–33.
IEEE, November 2013.
doi:10.1109/MSP.2013.104.
Invited paper.
[Details]
-
Cory T. Cornelius.
Usable Security for Wireless Body-Area Networks.
PhD thesis, Dartmouth College Computer Science, Hanover, NH, September 2013.
Available as Dartmouth Computer Science Technical Report TR2013-741.
[Details]
-
Shloka R. Kini.
Please Take My Survey: Compliance with smartphone-based EMA/ESM studies.
Technical Report number TR2013-734, Dartmouth Computer Science, Hanover, NH, May 2013.
Senior Honors Thesis.
[Details]
-
Aarathi Prasad, Ronald Peterson, Shrirang Mare, Jacob Sorber, Kolin Paul, and David Kotz.
Provenance framework for mHealth.
Proceedings of the Workshop on Networked Healthcare Technology (NetHealth), pages 1–6.
IEEE, January 2013.
doi:10.1109/COMSNETS.2013.6465599.
[Details]
- 2012:
-
Cory Cornelius and David Kotz.
Recognizing whether sensors are on the same body.
Journal of Pervasive and Mobile Computing, volume 8, number 6, pages 822–836.
Elsevier, December 2012.
doi:10.1016/j.pmcj.2012.06.005.
[Details]
-
Sasikanth Avancha, Amit Baxi, and David Kotz.
Privacy in mobile technology for personal healthcare.
ACM Computing Surveys, volume 45, number 1, article 3, 54 pages.
ACM, November 2012.
doi:10.1145/2379776.2379779.
[Details]
-
Aarathi Prasad, Ronald Peterson, Jacob Sorber, and David Kotz.
A Provenance Framework for mHealth.
Proceedings of the Workshop for Mobile Systems, Applications, and Services for Healthcare (mHealthSys) Poster Track, article 9, 2 pages.
ACM, November 2012.
doi:10.1145/2396276.2396287.
[Details]
-
Aarathi Prasad, Jacob Sorber, Timothy Stablein, Denise Anthony, and David Kotz.
Understanding Sharing Preferences and Behavior for mHealth Devices.
Proceedings of the Workshop on Privacy in the Electronic Society (WPES), pages 117–128.
ACM, October 2012.
doi:10.1145/2381966.2381983.
[Details]
-
Cory Cornelius, Jacob Sorber, Ronald Peterson, Joe Skinner, Ryan Halter, and David Kotz.
Who wears me? Bioimpedance as a passive biometric.
Proceedings of the USENIX Workshop on Health Security and Privacy, 10 pages.
USENIX Association, August 2012.
[Details]
-
Jacob Sorber, Minho Shin, Ron Peterson, and David Kotz.
Plug-n-Trust: Practical trusted sensing for mHealth.
Proceedings of the International Conference on Mobile Systems, Applications, and Services (MobiSys), pages 309–322.
ACM, June 2012.
doi:10.1145/2307636.2307665.
[Details]
-
Emma N. Smithayer.
Sensor-based system for verifying blood-pressure measurement position.
Technical Report number TR2012-720, Dartmouth Computer Science, Hanover, NH, June 2012.
Senior Honors Thesis.
[Details]
-
Cory Cornelius, Zachary Marois, Jacob Sorber, Ron Peterson, Shrirang Mare, and David Kotz.
Passive Biometrics for Pervasive Wearable Devices (Poster paper).
Proceedings of the Workshop on Mobile Computing Systems and Applications (HotMobile), 1 page.
ACM, February 2012.
[Details]
-
Aarathi Prasad.
Exposing Privacy Concerns in mHealth Data Sharing.
Master's thesis, Dartmouth College Computer Science, Hanover, NH, February 2012.
Available as Technical Report TR2012-711.
[Details]
- 2011:
-
Shrirang Mare, Jacob Sorber, Minho Shin, Cory Cornelius, and David Kotz.
Adapt-lite: Privacy-aware, secure, and efficient mHealth sensing.
Proceedings of the Workshop on Privacy in the Electronic Society (WPES), pages 137–142.
ACM, October 2011.
doi:10.1145/2046556.2046574.
[Details]
-
Shrirang Mare, Jacob Sorber, Minho Shin, Cory Cornelius, and David Kotz.
Hide-n-Sense: Privacy-aware secure mHealth sensing.
Technical Report number TR2011-702, Dartmouth Computer Science, September 2011.
[Details]
-
Shrirang Mare, Jacob Sorber, Minho Shin, Cory Cornelius, and David Kotz.
Adaptive security and privacy for mHealth sensing.
Proceedings of the USENIX Workshop on Health Security (HealthSec), 5 pages.
USENIX Association, August 2011.
Short paper.
[Details]
-
Aarathi Prasad, Jacob Sorber, Timothy Stablein, Denise Anthony, and David Kotz.
Exposing privacy concerns in mHealth.
Proceedings of the USENIX Workshop on Health Security (HealthSec), 2 pages.
USENIX Association, August 2011.
Position paper.
[Details]
-
Cory Cornelius and David Kotz.
Recognizing whether sensors are on the same body.
Proceedings of the International Conference on Pervasive Computing (Pervasive), volume 6696 in Lecture Notes in Computer Science, pages 332–349.
Springer-Verlag, June 2011.
doi:10.1007/978-3-642-21726-5_21.
[Details]
-
Jacob Sorber, Minho Shin, Ron Peterson, and David Kotz.
Poster: Practical Trusted Computing for mHealth Sensing.
Proceedings of the International Conference on Mobile Systems, Applications, and Services (MobiSys), pages 405–406.
ACM, June 2011.
doi:10.1145/1999995.2000058.
[Details]
-
David Kotz.
A threat taxonomy for mHealth privacy.
Proceedings of the Workshop on Networked Healthcare Technology (NetHealth), article 1, 6 pages.
IEEE, January 2011.
doi:10.1109/COMSNETS.2011.5716518.
[Details]
- 2010:
- 2009:
[Kotz research]
 Biometric identification/verification.
In this work we address two critical challenges. First, we evaluate
the use of bioimpedance for recognizing who is wearing
wireless sensors and show that bioimpedance is a feasible
biometric. Second, we investigate the use of accelerometers for
verifying whether two of these wireless sensors are on the same
person and show that our method is successful as distinguishing
between sensors on the same body and on different bodies. We stress
that any solution to these problems must be usable, meaning the user
should not have to do anything but attach the sensor to their body
and have them just work. This work is best described in Cornelius'
PhD thesis
[cornelius:thesis],
and also appeared in several papers
[cornelius:wearable,
cornelius:impedance,
cornelius:j-same-body,
cornelius:same-body,
cornelius:biometrics-poster].
We also conducted an early investigation into the prospect of
identifying people with their 'vocal resonance', that is, the sound of
their voice as recorded through their body
[cornelius:voice-tr];
this work later was finished under the
THaW project.
Biometric identification/verification.
In this work we address two critical challenges. First, we evaluate
the use of bioimpedance for recognizing who is wearing
wireless sensors and show that bioimpedance is a feasible
biometric. Second, we investigate the use of accelerometers for
verifying whether two of these wireless sensors are on the same
person and show that our method is successful as distinguishing
between sensors on the same body and on different bodies. We stress
that any solution to these problems must be usable, meaning the user
should not have to do anything but attach the sensor to their body
and have them just work. This work is best described in Cornelius'
PhD thesis
[cornelius:thesis],
and also appeared in several papers
[cornelius:wearable,
cornelius:impedance,
cornelius:j-same-body,
cornelius:same-body,
cornelius:biometrics-poster].
We also conducted an early investigation into the prospect of
identifying people with their 'vocal resonance', that is, the sound of
their voice as recorded through their body
[cornelius:voice-tr];
this work later was finished under the
THaW project.
