
NOTE:
The Center for Mobile Computing is no longer active, and this web site
represents a historical view of its activities from 1996-2008.
Although there is still mobile-computing research underway at
Dartmouth, we no longer update this web site. Please contact David Kotz with any
inquiries about the CMC.
[About CMC]
[Partners]
[Projects]
[Papers]
[People]
[News]
The CMC loosely categorizes its activities as Major Programs
or Individual Projects. This page lists Major Programs, which
generally correspond to a DARPA or DoD program, include multiple
technical projects, and have their own Web site. A separate page
lists Individual Projects below, many of
which are done under the auspices of one or more of the major
programs. This page lists only some CMC programs; we will expand
our coverage of CMC activities in the near future.
 D'Agents
D'Agents
A mobile agent is a program that can migrate under its own
control from machine to machine in a heterogeneous network.
Mobile agents allow some applications to make more effective use
of network resources by moving code to the network location of
the data, rather than pulling large volumes of intermediate
results back to the home machine. Mobile agents are particularly
attractive in wireless networks or other low-bandwidth,
unreliable network environments, and are best viewed as another
tool that programmers can use to develop the most effecient
distributed applications. The D'Agents program is a nine-year
effort that has developed a mobile-agent system, D'Agents, and
explored the performance, security, and applications of mobile
agents and other forms of mobile code.
 Active Communications
Active Communications
The ActComm project seeks to provide soldiers with wearable
computers and wireless data communications, and on top of this
infrastructure, various mission-support capabilities. The ActComm
project is a Multi-disciplinay University Research Initiative
(MURI), funded by the Department of Defense and administered by
the Air Force Office of Scientific Research. ActComm participants
are Dartmouth College, Harvard University, RPI, the University of
Illinois, Lockheed Martin - ATL, and ALPHATECH. Technical
projects under ActComm include ad-hoc wireless routing
algorithms, network sensing and prediction techniques, and
applications of mobile code.
 Control of Agent-Based Systems (CoABS)
Control of Agent-Based Systems (CoABS)
The CMC's CoABS program is part of DARPA's CoABS program, which
has over forty participating institutions looking at different
aspects of agent-based systems and programming. The CMC has
focused on resource control and scheduling algorithms for mobile
agents, mobile-code performance and scalability, and
interoperability middleware for mobile-agent systems.
This page lists some of the CMC Projects. The dates associated
with each project indicate when the project description was
written, and where possible, we provide links to people or pages
that have more recent information.
- Data Assurance in Medical Sensor Applications
2007
-
We expect that wearable, portable, and even embeddable
medical sensors will enable long-term continuous medical
monitoring for many purposes, such as patients with chronic
medical conditions (such as the recently announced
blood-sugar sensors for diabetics), people seeking to change
behavior (e.g., losing weight, or quitting smoking), or
athletes wishing to monitor their condition and performance.
The resulting data may be used directly by the person, or
shared with others: with a physician for treatment, with an
insurance company for coverage, or by a trainer or coach.
Such systems have huge potential benefit to the quality of
healthcare and quality of life for many people.
Since the sensor data may be gathered through a patient's
mobile device (such as a mobile phone), a wireless network,
and the Internet, there are many opportunities for the sensor
data to be tampered or otherwise inaccurate. How can we
assess confidence in sensor data? How can we present that
level of confidence, in context, with the sensor data? This
project will develop methods to assess confidence in medical
sensor data.
Funded by the Intel University Research Council.
- MetroSense: scalable secure sensor systems
September, 2006
-
Sensor networks will provide a foundation to protect and
monitor our national infrastructure, including economically
important businesses with global reach (e.g., stock markets),
critical transport and industrial facilities, the enterprise,
and the border. These tiny, low-cost wireless devices embed
on-board sensing, are fully programmable, and can
spontaneously form large sensor webs with thousands of
distributed sensor devices. In this project, we will study,
analyze, propose, deploy, and evaluate MetroSense, a
radically different scalable secure sensor architecture and
system capable of reliable real-time monitoring and data
fusion for large-scale critical infrastructure, resources,
and assets. MetroSense opportunistically leverages mobile
sensors when available to deal with sparse coverage and
communications when sensing. We plan to develop a campus-area
sensing architecture based on three integrated components
(sensing and communications, sensor security, and sensor
fusion) and deploy the system incrementally across campus
with the goal of using static and mobile sensors for reliable
monitoring and data fusion of campus plant, spaces, and
people flow. Results from this project will serve as a
foundation for building secure sensor networks capable of
monitoring large-scale critical infrastructure.
- CRAWDAD: a Community Resource for Archiving Wireless
Data at Dartmouth.
July, 2005
http://crawdad.cs.dartmouth.edu/
-
As a community resource, the CMC is building an archive
with the capacity to store wireless trace data from many
contributing locations, with the staff to develop better
tools for collecting, anonymizing, and analyzing the data.
This Community Resource for Archiving Wireless Data At
Dartmouth, CRAWDAD, will work with community leaders to
ensure that the archive meets the needs of the research
community, work with the other leading centers that develop
network tracing tools and metadata, and work with research
organizations and corporations to ensure continuing support
for the archive after NSF's funding ends.
Older CMC projects
- Real Time Monitoring of a Wireless Mesh Network for
Emergency Response Operations
Soumendra Nanda and David Kotz
July, 2005
-
Wireless mesh networks can be used to provide
communication infrastructure for emergency response
operations in areas with limited or damaged infrastructure.
We imagine the formation of a wireless mesh of heterogeneous
devices such as transceivers on ambulances, fire trucks and
police cars. This mesh would support a network of Personal
Digital Assistants (PDAs) on first responders and an ad hoc
network of rapidly deployed micro-sensor devices. Monitoring
of such a mesh network will be crucial to the success of
first responder operations. Standard techniques for
monitoring wired networks or even wireless infrastructure
networks are unsuitable for a wireless mesh network with
unpredictable links and resource-constrained devices. Our
goal is to develop a wireless mesh monitoring system to
detect and identify real-time problems and aid system
administrators in making proactive as well as reactive
management decisions.
We propose to develop a mesh monitoring system that can be
used to generate real-time network topology maps, power maps
and provide real-time data on network traffic and user
locations to aid mission planners. The aim of this project is
to present new ways to efficiently implement a real-time
wireless monitoring system that assists in fault detection,
repair and the automation of network management tasks. It may
also be possible to use the monitored information about the
state of the network to improve and optimize the performance
of the mesh routing protocol. Some other contributions of
this work will be in the use of error codes to recover
information from corrupt or lost packets and to maximize
utility of monitoring information sent over an unreliable
channel. Our initial plan is to deploy a 15-node multi-radio
mesh network and to monitor it using in-band channels as well
as out-of-band channels (such as a wired backhaul or a
separate wireless channel) for the traffic being monitored.
Thus we can study the effectiveness of the monitoring system
and its impact on the behavior of the mesh network. In
parallel, we will simulate a mesh network to study
scalability and other characteristics of the monitoring
system.
- Digital Living: Understanding PLACE (Privacy in
Location-Aware Computing Environments)
Faculty: Denise Anthony, Andrew Campbell, David Kotz (lead),
Tristan Henderson
Staff: Ronald Peterson
July, 2005
-
Digital technology plays an increasing role in everyday
life, and this trend is only accelerating. Consider daily
life five years from now, in 2010: we will each be surrounded
by far more digital devices, mediating far more activities in
our work, home, and play; the boundary between cyberspace and
physical space will fade as sensors and actuators allow
computers to be aware of, and control, the physical
environment; and the devices in our life become increasingly
(and often invisibly) interconnected with each other and with
the Internet. Today, typical home users struggle to maintain
the security of their home computer, and have difficulty
managing their privacy online. Tomorrow, these challenges may
become unimaginably complex. This 18-month project studies,
and begins to address, the security and privacy challenges
involved in developing this world of Digital Living in
2010.
Specifically, this project focuses on the advent of sensor
networks, and their applications in the home and work
environment. Although sensor networks have been an active
area of academic research, and are becoming commercially
available for deployment in industrial settings, sensor
networks will soon have many uses in enterprise and
residential settings. People will live in spaces, or work
with devices, that have embedded sensing capability. For
people to accept this new technology into their lives, they
must be able to have confidence that the systems work as
expected, and do not pose unreasonable threats to personal
privacy. This confidence results from a variety of technical
and organizational mechanisms. This project delves into the
sociological underpinnings of privacy and trust in digital
living, into the technological foundations for secure and
robust sensor networks, and into mechanisms for users to
express control over information about their activity.
- MAP: Measure, Analyze, Protect: Security through
measurement for Wireless LANs.
July, 2005
http://www.cs.dartmouth.edu/~map/
-
With the rise of Voice over wireless LAN (VoWLAN), any
complete WiFi security solution must address denial of
service attacks, such as kicking off other clients, consuming
excessive bandwidth, or spoofing access points, to the
detriment of legitimate clients. Even authorized clients may
be able to sufficiently disrupt service quality to make the
network ineffective for legitimate clients. Our approach
provides a new foundation for wireless network security, able
to dynamically measure, analyze and protect a WiFi network
against existing and novel threats, including rogue clients
and access points, with a focus on VoWLAN use cases. Our goal
is to support thousands of APs and clients, quickly recognize
most new attacks, and generate few false alarms.
- Automated Remote Triage and Emergency Management
Information System
May, 2005
Susan McGrath, Bob Gray, George Blike, Stephen Linder,
Christopher Carella, Janelle Chang, Michael De Rosa, Aaron
Fiske, Curtis McClurkin, Suzanne Wendelken
-
 The Automated Remote Triage and
Emergency Management Information System (ARTEMIS) is an
ongoing research effort at Dartmouth College's Institute for
Security Technology Studies that aims to provide real-time
physiological information to first responders and command
personnel in emergency/disaster situations. The prototype
system is capable of monitoring and assessing physiological
parameters of individuals, transmitting pertinent medical
data to and from multiple echelons of medical service
personnel, and providing filtered data for command and
control applications.
The Automated Remote Triage and
Emergency Management Information System (ARTEMIS) is an
ongoing research effort at Dartmouth College's Institute for
Security Technology Studies that aims to provide real-time
physiological information to first responders and command
personnel in emergency/disaster situations. The prototype
system is capable of monitoring and assessing physiological
parameters of individuals, transmitting pertinent medical
data to and from multiple echelons of medical service
personnel, and providing filtered data for command and
control applications.
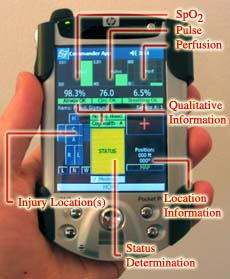 The system employs wireless
networking, portable computing devices, and reliable
messaging technology as a framework for information analysis,
information movement, and decision support capabilities.
Physiological status assessment is based on a medical model
that relies on input from humans and a pulse oximetry device.
Our physiological status determination methodology follows
NATO defined guidelines for remote triage and is implemented
using an approach based on fuzzy logic. The approach
described on this website can be used in both military and
civilian settings.
The system employs wireless
networking, portable computing devices, and reliable
messaging technology as a framework for information analysis,
information movement, and decision support capabilities.
Physiological status assessment is based on a medical model
that relies on input from humans and a pulse oximetry device.
Our physiological status determination methodology follows
NATO defined guidelines for remote triage and is implemented
using an approach based on fuzzy logic. The approach
described on this website can be used in both military and
civilian settings.
The long-term goal of the ARTEMIS project is to integrate
advances in communications and analysis technologies into a
remote triage system that can expedite and improve care of
the wounded in small-to-large scale emergency situations. Our
aim is to provide an unprecendented degree of medical
situational awareness at all levels of the first-responder
command heirarchy.
- Mobility modeling
April, 2005
Minkyong Kim, David Kotz
-
Many people who design, develop, or deploy wireless
networks use simulations to evaluate the impact of their
design decisions on the performance of the network. For these
simulations to be effective, however, one must have a
realistic model of device mobility. Currently available
models of device mobility do not reflect the movement
patterns of real users. Using the traces collected by access
points (APs) on our campus, we aim to develop realistic
mobility models.
 We are interested in
developing models of both AP-association patterns and
physical user movements. The former presents how mobile users
roam from one AP to another, while the latter describes how
mobile users move in a physical space. To develop an
association model, we first extract the characteristics of
association patterns directly from the syslog messages
(available on this site). We then derive an association model
from these characteristics. To develop a physical-mobility
model, however, we first need to estimate the physical
location of users from the association patterns; this task is
not easy because a mobile device does not necessarily
associate with the geographically-closest AP. Our path
extractor estimates paths from AP-association patterns and
has been validated against GPS track data as shown in the
figure. These extracted paths are used for developing a
physical-mobility model.
We are interested in
developing models of both AP-association patterns and
physical user movements. The former presents how mobile users
roam from one AP to another, while the latter describes how
mobile users move in a physical space. To develop an
association model, we first extract the characteristics of
association patterns directly from the syslog messages
(available on this site). We then derive an association model
from these characteristics. To develop a physical-mobility
model, however, we first need to estimate the physical
location of users from the association patterns; this task is
not easy because a mobile device does not necessarily
associate with the geographically-closest AP. Our path
extractor estimates paths from AP-association patterns and
has been validated against GPS track data as shown in the
figure. These extracted paths are used for developing a
physical-mobility model.
- WLAN User Mobility Prediction
April, 2005
Libo Song, Udayan Deshpande, David Kotz, Ravi Jain, Ulas Kozat,
and Xiaoning He
-
In wireless networks users can move from one location to
another location without losing their network connection.
This flexibility of mobility introduces new challenges in
quaranteeing quality of service (QoS) and in locating users
and transfering data between them and the access points
(APs). By predicting a user's next AP we can reduce the
overhead of mobility management and make bandwidth
reservations to guarantee the QoS.
Many prediction algorithms have been proposed, but most of
them are evaluated by simulations using synthetic data. We
have collected the association messages at our campus-wide
wireless network. From the association messages, we extracted
the mobility traces, and evaluated prediction methods
using our real wireless mobility data. We found that
low-order Markov predictors performed as well or better than
the more complex and more space-consuming compression-based
predictors.
Besides predicting the next AP, anticipating a user's
handoff time is also important for applications such as
bandwidth reservation, which needs to know when to reserve
bandwidth. It is easier to estimate the handoff probability
with a period of time than to predict the exact time. We
developed such a time predictor and combined it with a
location predictor to compute the probability that a user
handoffs to a certain AP within a given period of time. We
simulated several bandwidth reservation schemes using this
location-and-time-integrated predictor with our real mobility
data. The results show that both call-drop rate and
call-block rate are reduced significantly.
Since our simulation indicates that with accurate
location-and-time prediction the QoS of calls is improved, we
would like to improve the performance of predictors. In the
future, we will continue to collect wireless association data
and investigate the characteristics of users mobility
patterns. We believe these mobility characteristics will help
us develop better predictors.
- Guiding People and Robots with Sensor Networks
March, 2005
Daniela Rus, Ronald Peterson, Peter Corke, Gaurav Sukhatme,
Srikanth Saripalli, Stefan Hrabar
-
 A wireless sensor network can extend the
sensory perception of people and robots far beyond their
normal range. Wireless sensors are also small computers. When
the sensors are used to detect danger they can perform
distributed computations to compute the safest path along
which a person or robot can be guided. Sensors that detect
their own network connectivity can be used to guide a robot
to repair holes in that connectivity. Sensors that detect a
fault in an industrial process can guide a robot or person to
the location of the fault for further inspection. Robots and
people can also store information in a sensor network which
can later be used for guidance, or by the sensor network
itself (for example by telling the sensors their GPS
coordinates.)
A wireless sensor network can extend the
sensory perception of people and robots far beyond their
normal range. Wireless sensors are also small computers. When
the sensors are used to detect danger they can perform
distributed computations to compute the safest path along
which a person or robot can be guided. Sensors that detect
their own network connectivity can be used to guide a robot
to repair holes in that connectivity. Sensors that detect a
fault in an industrial process can guide a robot or person to
the location of the fault for further inspection. Robots and
people can also store information in a sensor network which
can later be used for guidance, or by the sensor network
itself (for example by telling the sensors their GPS
coordinates.) 
We have been exploring all these concepts in a large variety
of experiments. In the picture on the right, USC's AVATAR
autonomous flying robot is repairing the gaps in connectivity
in a sensor network. The sensor network computed the
locations of missing sensors, the robot queried the network
for the gap location, and then flew over the gap, dropping
new sensors to repair the network.
In the picture on the left, a crane robot at CMU is
interacting with a sensor network. The robot is controlled by
precision winches connected to the four cables attached to
the robot from the ceiling. This type of robot might be used
inside a factory to maintain sensors that monitor industrial
processes. The robot first broadcasts location messages while
moving in a precise pattern to localize the sensors. A radio
message was then broadcast to the sensor network and followed
a precise geographic path through the sensors. The robot then
queried the sensors to follow the same path as the radio
message.
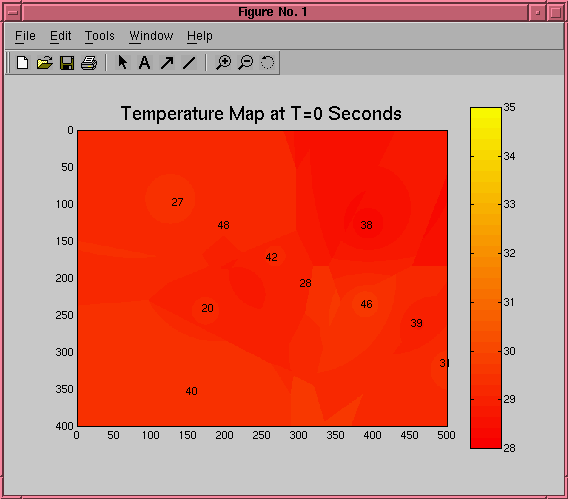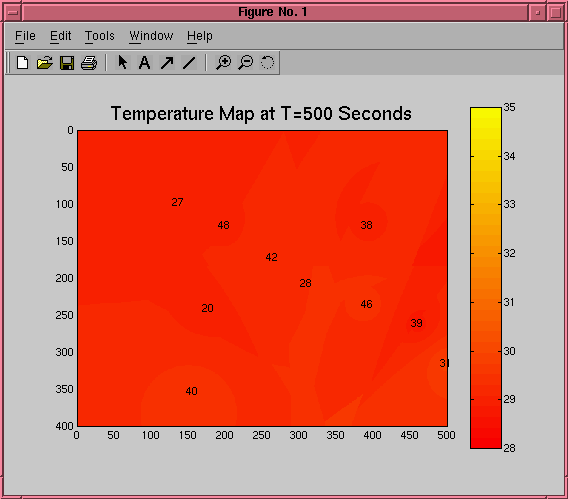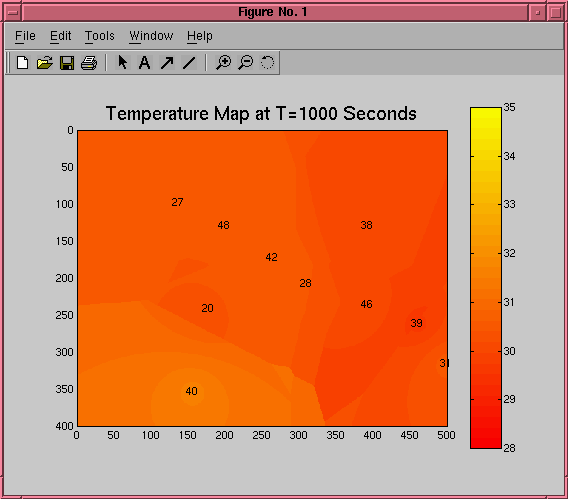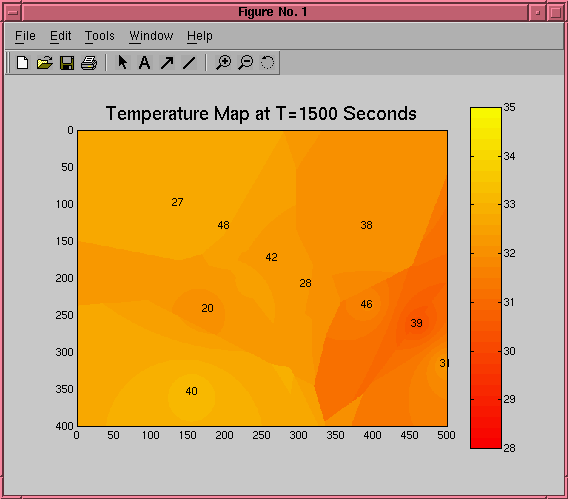 We have also been looking at using maps of
sensed data to guide people and robots. The picture on the
left shows a temperature map as it varies over time in a room
where a large fire has been started. Guidance algorithms can
make use of such maps to bring people to safety, or to guide
firefighters to the danger.
We have also been looking at using maps of
sensed data to guide people and robots. The picture on the
left shows a temperature map as it varies over time in a room
where a large fire has been started. Guidance algorithms can
make use of such maps to bring people to safety, or to guide
firefighters to the danger.
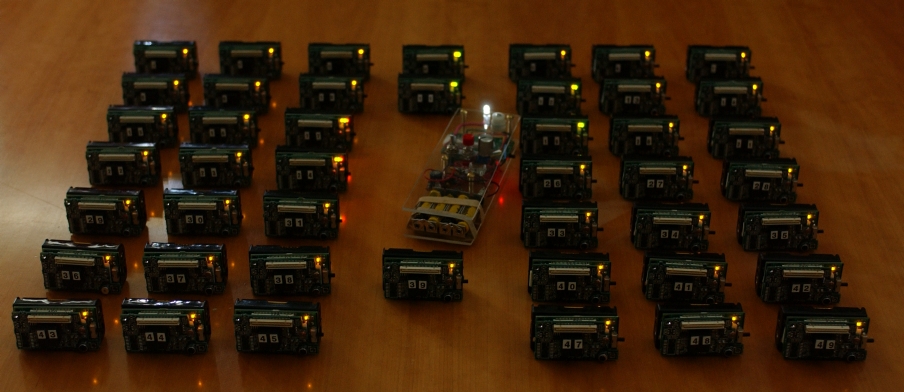
A device we call a "flashlight", shown in the center of the
sensors in the picture below, can be carried by a person or
robot to find their way through an area based on the data
stored in the sensors or on the readings from the
sensors.
- Quality-managed Group-aware Stream Filtering
November, 2007
Ming Li, David Kotz
-
This project considers a distributed system that
disseminates high-volume data streams to many simultaneous
monitoring applications over a low-bandwidth network. For
bandwidth efficiency, we propose a group-aware stream
filtering approach, used together with multicasting, that
exploits two overlooked, yet important, properties of
monitoring applications: 1) many of them can tolerate some
degree of ``slack'' in their data quality requirements, and
2)there may exist multiple subsets of the source data
satisfying the quality needs of an application. We can thus
choose the ``best alternative'' subset for each application
to maximize the data overlap within the group to best benefit
from multicasting. Here we provide a general framework for
the group-aware filtering problem, which we prove is NP-hard.
We introduce a suite of heuristics-based algorithms that
ensure data quality (specifically, granularity and
timeliness) while preserving bandwidth.
Our work exploits applications' semantics to better
managing precious network resources. For evaluation, we
integrate group-aware filtering with a general-purpose sensor
data dissemination middleware system, Solar, developed at
Dartmouth College. Our evaluation shows that quality-managed
group-aware filtering is effective in trading CPU time for
bandwidth savings, compared with self-interested stream
filtering.
- Measuring
Wireless Networks
March, 2005
Tristan Henderson, David Kotz, Denise Anthony
-
IEEE 802.11 Wireless Local Area Networks (WLANs) are now
commonplace on many academic and corporate campuses. As
“Wi-Fi” technology becomes ubiquitous,
understanding trends in the usage of these networks becomes
increasingly important for network deployment, management,
and the development of new wireless and location-aware
applications. We have been measuring various aspects of
Dartmouth's campus-wide WLAN since the installation of the
network in 2001. The extensive coverage of Dartmouth's WLAN
allows us to study how the network is used by students,
faculty and staff.
We employ a variety of methods to measure wireless network
usage. We have deployed “sniffer” boxes (Linux
PCs with multiple network interfaces) around the campus to
observe the data packets that are transferred over the
network; this enables us to measure wireless application
usage. By using SNMP and syslog to monitor the access points
we can measure user mobility patterns. We have also deployed
wireless sniffers to measure the 2.4GHz and 5GHz frequency
bands that are used by IEEE 802.11a/b/g networks; this allows
us to measure wireless traffic that does not traverse the
wired side of the Dartmouth network, and also lets us observe
other wireless networks, such as ad-hoc networks or
“rogue” access points. Finally, we are also
investigating the use of psychological methodologies, such as
the Experience Sampling Method, to ask the network users
themselves about their experiences with the wireless
network.
We have discovered that since the deployment of the
network, usage has moved away from non-realtime applications
such as the World Wide Web, with an increasing amount of
streaming audio/video and peer-to-peer file transfers being
conducted over the WLAN. Although Dartmouth has migrated to a
Voice over IP telephone system, we have seen little wireless
VoIP usage. We encourage other researchers to make use of the
data that we have collected, and anonymised datasets are
available on CRAWDAD.
- Mobile Sensors for First Responders
March, 2005
Ron Peterson, Daniela Rus
-
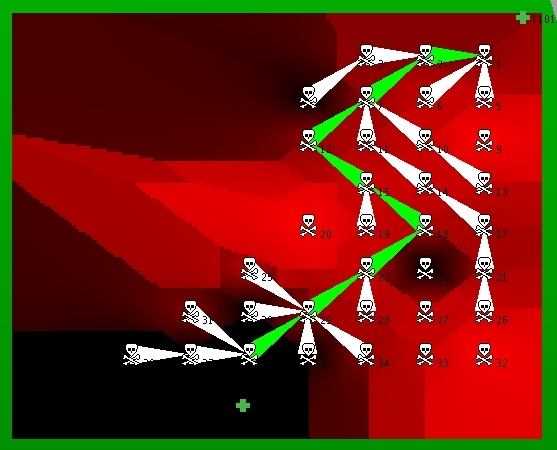
In many emergency calls the presense of
deadly, invisible chemicals is first noticed when people
start coughing or falling ill. Even after the presence of a
toxin has been verified, unless visible it is difficult to
avoid exposure due to air motion. Networks of mobile chemical
sensors (sensors on robots) can provide a first warning of
nearby toxins, and tell us where they are, where they are
moving towards, and how to avoid them.
As part of ongoing work in medical and environmental sensors
for first responders, we devised a simulated air crash
scenario that involves a chemical leak. The crash throws some
debris into a nearby farmers field where a tank of anhydrous
ammonia used as fertilizer is present on a trailer attached
to a tractor.  Anhydrous ammonia, when released into the
atmosphere, is a clear colorless gas, which remains near the
ground and drifts with the wind. It attacks the lungs and
breathing passages and is highly corrosive, causing damage
even in relatively small concentrations. It can be detected
with an appropriate sensor such as the Figaro TGS 826 Ammonia
sensor. Our experiments map the presence of an ammonia
cloud and guide a first responder to safety along the path of
least chemical concentration. The image on the right shows
such a danger map with the safest path computed by a network
of 38 Mica Mote sensors.
Anhydrous ammonia, when released into the
atmosphere, is a clear colorless gas, which remains near the
ground and drifts with the wind. It attacks the lungs and
breathing passages and is highly corrosive, causing damage
even in relatively small concentrations. It can be detected
with an appropriate sensor such as the Figaro TGS 826 Ammonia
sensor. Our experiments map the presence of an ammonia
cloud and guide a first responder to safety along the path of
least chemical concentration. The image on the right shows
such a danger map with the safest path computed by a network
of 38 Mica Mote sensors.
We are currently exploring the utility of mobile sensor
networks in warning, guidance, and sensing for search and
rescue missions in the difficult environments created by
disaster situations, such as the rubble pile from a destroyed
building shown to the left.
- Mobile Computers for Herding Cattle with Virtual
Fences
March, 2005
Daniela Rus, Ronald Peterson, Peter Corke, Zack Butler
-

Fences on open ranges cost the cattle
industry a lot of time and money to install and maintain.
Herding cattle also involves much time and effort. A
collaboration between Daniela Rus, the CSIRO Robotics Team in
Australia and a USDA Ranch Management Research Animal
Scientist was initiated at Dartmouth to consider the problem
of monitoring and controlling the position of herd
animals.
 The goal is to apply the vast body of
theory in robotics and motion planning to virtual fences for
controlling animals and to integrate new technologies, such
as wireless adhoc networking, into a field where technology
has yet had little penetration. Similar to the "invisible
fence" products sold for fencing pets in the yard at home, a
virtual fence is a collar or tag worn by an animal which
tracks its location via GPS and applies a stimulus to the
animal to control its motion. Animals are not robots and
their unpredictable reactions mean that existing robotics
motion control solutions must be modified to take into
account the imprecise control before they can be useful.
The goal is to apply the vast body of
theory in robotics and motion planning to virtual fences for
controlling animals and to integrate new technologies, such
as wireless adhoc networking, into a field where technology
has yet had little penetration. Similar to the "invisible
fence" products sold for fencing pets in the yard at home, a
virtual fence is a collar or tag worn by an animal which
tracks its location via GPS and applies a stimulus to the
animal to control its motion. Animals are not robots and
their unpredictable reactions mean that existing robotics
motion control solutions must be modified to take into
account the imprecise control before they can be useful.
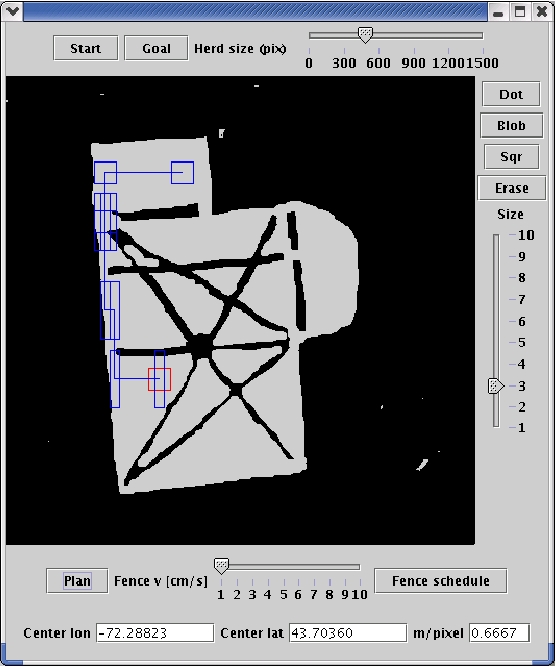
 The picture on the upper right shows a cow
wearing an early prototype of a Smart Collar during an
experiment. The picture on the lower left shows an automatic
path planner for herding animals around obstacles to a goal.
The picture on the lower right shows another early Smart
Collar prototype with a PDA, adhoc WiFi multihop networking,
GPS, and sound system for producing stimuli.
The picture on the upper right shows a cow
wearing an early prototype of a Smart Collar during an
experiment. The picture on the lower left shows an automatic
path planner for herding animals around obstacles to a goal.
The picture on the lower right shows another early Smart
Collar prototype with a PDA, adhoc WiFi multihop networking,
GPS, and sound system for producing stimuli.
- Security and access-control in context-aware
computing
Kazuhiro Minami, David Kotz
August, 2005
-
 In pervasive computing, many
applications will be context-aware; that is, the applications
adapt their behaviors according to user's situation or
environment. We are examining the potential for making
authorization decisions (such as access to a medical
database) based on the context of the user making the
request. Such a context-sensitive authorization scheme is
necessary when mobile users (e.g., first responders) move
across multiple administrative domains where they are not
registered into the systems in advance. For example, in the
First Responder project, a granting decision could depend on
a requester's current location or medical conditions, which
is obtained from the information servers. The information
servers, in return, collect situational information from a
sensor network that covers an emergency area. Since context
information, such as the location of the user, might allow an
malicious party to infer the user's private information, we
particularly address the issue of protecting confidential
information involved in authorization policies to protect the
users' privacy.
In pervasive computing, many
applications will be context-aware; that is, the applications
adapt their behaviors according to user's situation or
environment. We are examining the potential for making
authorization decisions (such as access to a medical
database) based on the context of the user making the
request. Such a context-sensitive authorization scheme is
necessary when mobile users (e.g., first responders) move
across multiple administrative domains where they are not
registered into the systems in advance. For example, in the
First Responder project, a granting decision could depend on
a requester's current location or medical conditions, which
is obtained from the information servers. The information
servers, in return, collect situational information from a
sensor network that covers an emergency area. Since context
information, such as the location of the user, might allow an
malicious party to infer the user's private information, we
particularly address the issue of protecting confidential
information involved in authorization policies to protect the
users' privacy.
 We developed a secure logic-based
authorization system where authorization policies are
expressed as logical rules (i.e., Horn clauses). A request is
granted if the authorization server succeeds in constructing
a proof tree that derives the granting decision. Our
decentralized scheme does not need a universally trusted
central authorization server that maintains all the context
information; the authorization decisions are made by multiple
hosts, each of which only has partial knowledge about the
context information, in a peer-to-peer way. Our novel
distributed algorithm decomposes a proof tree into multiple
subproof trees produced by different hosts so that
confidentiality policies of each host are satisfied. We are
deploying our current implementation into an emergency
response system to evaluate the performance and scalability
of the system.
We developed a secure logic-based
authorization system where authorization policies are
expressed as logical rules (i.e., Horn clauses). A request is
granted if the authorization server succeeds in constructing
a proof tree that derives the granting decision. Our
decentralized scheme does not need a universally trusted
central authorization server that maintains all the context
information; the authorization decisions are made by multiple
hosts, each of which only has partial knowledge about the
context information, in a peer-to-peer way. Our novel
distributed algorithm decomposes a proof tree into multiple
subproof trees produced by different hosts so that
confidentiality policies of each host are satisfied. We are
deploying our current implementation into an emergency
response system to evaluate the performance and scalability
of the system.
Greenpass: Decentralized Authorization in Wireless
Networks
July 2004
Sean Smith
Agent Based Casualty Care (ABC Care)
October 2003
Susan McGrath
- The goal of the ABC Care project is to integrate advances
in communications and analysis technologies into a combat
casualty care system which can expedite and improve the care of
wounded soldiers. The ABC Care prototype is capable of
monitoring and assessing physiological parameters of individual
soldiers, transmitting pertinent medical data to and from
multiple echelons of medical personnel, and delivering
treatment protocols. ABC Care employs mobile agent technology
as the framework for information analysis, movement, and
decision support capabilities. Medical models and physiological
status assessment are based on input from humans and a pulse
oximeter. The physiological status determination methodology
follows NATO defined guidelines and is implemented using an
approach based on fuzzy logic.
Analysis of the campus-wide wireless network and the impact
of VoIP
September 2003
David Kotz
- Dartmouth College has a campus-wide WiFi network with over
560 Cisco access points. In our previous work we extensively
characterized the nature of WiFi usage by over 3000 campus WiFi
users, data that has been significantly useful to network
planners, network designers, and application developers. Today,
we are replacing our campus telephone system with a complete
Cisco VoIP solution, installing over 6000 Cisco VoIP phones and
SoftPhones in the next two years. We expect many SoftPhones and
WiFi handsets to be in use, so VoIP should have a significant
impact on our wireless network. We will take advantage of this
incredible opportunity to monitor our wireless network before
and after the introduction of wireless VoIP clients, to measure
the characteristics of voice users and their traffic, to
measure the load on the wireless network, and to evaluate the
impact of voice on the Cisco access points and on the
network.
The
Bear/Enforcer Project
September 2003
Sean
Smith
- How can you verify that a remote computer is the "real
thing, doing the right thing?" High-end secure coprocessors are
expensive and computationally limited; lower-end desktop
enhancements like TCPA and the former Palladium have been
mainly limited to Windows and proprietary development.
In contrast, this code is part of our ongoing effort to use
open source and TCPA to turn ordinary computers into "virtual"
secure coprocessors---more powerful but less secure than their
high-assurance cousins.
The Linux Enforcer Module is a Linux Security Module designed
to help improve integrity of a computer running Linux. The
Enforcer provides a subset of Tripwire-like functionality. It
runs continuously and as each protected file is opened its SHA1
is calculated and compared to a previously stored value. More
information about this project and a recent paper can be found at
this
Dartmouth Technical Report TR2003-17 as well as the Enforcer Sourceforge
site
Spatial Multipath Location Aided Ad Hoc Routing
August 2003
Soumendra Nanda, Robert Gray
Mobile ad-hoc networks (MANETs) are infrastructure free
networks of mobile nodes that communicate with each other
wirelessly.Our goal is to utilize three-dimensional (3D) position
information to provide more reliable as well as efficient
routing. We thus describe extensions to various location aware
routing algorithms to work in 3D. We propose a new hierarchical,
zone-based 3D routing algorithm, based on GRID by Liao, Tseng and
Sheu. Our new algorithm called "Hyper-GRID" is a hybrid algorithm
that uses multipath routing in 3D.
We wish to implement a multipath algorithm similar to AOMDV in
Hyper-GRID as we expect to see lower end-to-end delays, lower
packet loss and reduced routing overhead by reducing the
frequency of route discovery phases through use of a multipath
routing strategy.
Context-aware pervasive computing
February 2003
David Kotz, Guanling Chen, Kazuhiro Minami
The Solar project is
using the campus wireless network, as well as a location-tracking
system developed by Versus
Technologies and installed in the computer-science building,
to investigate the potential for location-aware applications and
for pervasive computing in general.Kotz and his students are
developing a flexible and secure infrastructure to collect,
process, and disseminate location and other contextual
information to context-aware applications; prototyping
location-aware and context-aware applications, both in a campus
setting and in emergency-response scenarios.
Their Solar System is a software infrastructure that supports
context collection, aggregation, and dissemination. Solar
provides a small composition language, allowing applications to
construct a graph of operators to compute desired context from
appropriate sources. Solar implements a context-sensitive
resource discovery mechanism to achieve flexibility, and improves
the scalability by balanced distribution and reuse of
operators.
Location-aware applications in education
February 2003
Ted Cooley
Professor Cooley at Thayer School of Engineering and Newbury Networks have teamed
to install Newbury's Locale Points within the Engineering School.
Now, a user with a wireless-enabled TabletPC, notebook, of PDA is
pushed web content depending on whether they are standing in the
reception area, working in a computer lab, taking a class, etc.
Thus, welcome information, how to get help, or class notes can be
easily provided to the user.
An example project currently underway to take advantage of
this location technology is Multimedia Techniques for Engineering
Instruction, MTEI. With this system, course materials for
specific courses, offered at specific times are wirelessly
delivered to students in a given classroom. The MTEI system is
also use for online quizzes for credit, and anonymous assessment
to gauge whether the class is understanding a particular point or
not. The latter results are displayed on the, "clue meter", a
web-based gauge of student understanding.
Guiding Navigation across a Sensor Network
December 2002
Daniela Rus, Qun Li, Michael DeRosa, Ron Peterson
We develop distributed algorithms for self-reconfiguring
sensor networks that help direct an object (say, a soldier or a
robot) through a dangerous region. The sensor network models the
danger levels sensed across its area, representing the dangerous
areas as obstacles. A protocol that combines the artificial
potential field of the sensors with the object's goal location
guides the moving object incrementally across the network to the
goal, while maintaining the safest distance to the danger areas.
To evaluate the performance of the algorithms, we have done many
hardware experiments using a physical sensor network consisting
of Berkeley's Mote sensors.
Power-aware Protocols in
Sensor Networks
December 2002
Javed Aslam, Daniela Rus, and Qun Li
We develop online power-aware routing algorithms in large
wireless ad-hoc networks for applications where the message
sequence is not known. We seek to optimize the lifetime of the
network. We develop a series of approximation algorithms to solve
the problem, including the centralized max-min zPmin algorithm,
hierarchical algorithm, and several distributed algorithms that
can reduce the message broadcasts on each node. Our experiments
show that the performance is quite good. We are also working on
the MAC-layer protocols to conserve energy by putting nodes into
sleeping mode.
Communication and Exploration in Mobile Sensor
Network
December 2002
Daniela Rus and Qun Li
Mobile sensor networks are a new form of sensor network in
which the sensors are tethered to some moving equipment, such as
wheels or flying objects. We study how the sensors can
reconfigure themselves to achieve better network connectivity,
message transmission, and other group behaviors. We developed
algorithms to guarantee message delivery in a disconnected mobile
sensor network by asking mobile sensors to move. Our next task is
to develop algorithms for a mobile sensor network to explore a
large area.
- Semantic Sensor Networks
November 2002
Glenn Nofsinger and George Cybenko
Our research focuses on how to integrate battlefield
information systems in a dynamic information environment to
support information exploitation. Our goal is to create greater
semantic interoperability among sensors and information assets.
Our wireless sensor platform currently uses a hybridization of
WiFi, 900 Mhz Spread Spectrum, GPS, and Dartmouth designed MiniME
GPS sensors. Sensor measurements include sound, temperature, and
seismic vibrations. These measurements are combined with a
variety of data fusion algorithms distributed across the
network.
Greenwave Wireless
November 2002
Chris Lentz and Zach Berke (not formally affiliated with
CMC)
Two students are installing private APs in off-campus
residences, and configuring them as repeaters. The goal is to
expand the reach of the campus wireless network into private
residences nearby. They route wireless traffic into the on-campus
APs and thence to the campus backbone and the Internet. As a
result we are getting valuable early experience with the
realities of repeaters and mesh technologies.
Former CMC Projects
Network mapping
February 2003
David Kotz, Cal Newport, Chris Lentz
- We plan to develop algorithms and technology for real-time
mapping of the network's signal characteristics, using the
existing infrastructure APs as sensors and using SNMP to
collect the necessary data. One goal of this project is to
improve the quality of the network models that are frequently
used to analyze and validate routing algorithms for ad-hoc and
mesh networks. Preliminary results show that signal strength
between two stationary access points is substantially
asymmetric, and that distance does not correlate well with
signal strength.
Tacos Wireless Device Tracking System
November 2002
Chris Lentz and Zach Berke (not formally affiliated with
CMC)
Tacos is a web site allowing users to register any wireless
device by listing its MAC address, after authenticating through
our campus authentication database. If a device is ever lost or
stolen, they use the website to report it as missing. If the
device is ever activated on the Dartmouth Campus, they receive an
immediate email indicating the device location. The location is
derived from the associated AP name.
Market-based resource control
June 2001
Jon Bredin, Ph.D '01
Jon used ideas from economics to develop a market-based
approach to the allocation of resources in a distributed system.
In his approach, computations are mobile agents that need to jump
from host to host to reach the resources they need. They must pay
for the computation time they use at each host. The resulting
market is an efficient mechanism for fair, distributed allocation
of computational resources. In the fall Jon will be a professor
in the Mathematics and Computer Science department at Colorado
College.
Scalable directory for mobile users
June 2001
Ammar Khalid '01
Ammar developed a secure, scalable directory service for
mobile users, and applied it to the mobile voice-over-IP
application developed by Ayorkor. Chief among its goals was
protecting the privacy of mobile users, so that a stalker cannot
track the IP address (and thus the location) of a moving user.
For his work, Ammar was awarded High Honors and shared the Kemeny
Prize for Computing.
Mobile Voice-over-IP
June 2001
Ayorkor Mills-Tettey '01
Ayorkor extended the H.323 telephony protocols so that a
voice-over-IP conversation can continue even as the mobile user's
computer roams from access point to access point, and from IP
subnet to IP subnet, changing IP addresses. For her work, Ayorkor
was awarded High Honors and shared the Kemeny Prize for
Computing.
SmartReminder
June 2001
Arun Mathias '01
Arun implemented the first application for Guanling Chen's
Solar system. His SmartReminder application reminds its user of
upcoming appointments depending on the current location and the
location of the next appointment. For his work, Arun was awarded
High Honors and shared the Kemeny Prize for Computing.
Characterizing the use of Dartmouth's wireless
network
June 2001
Pablo Stern '01 and Kobby Essien '02
Pablo used SNMP and an IP sniffer to trace the activity of
the new campus wireless network, to characterize the way that
people use the network. For his work, Pablo was awarded High
Honors.
Geographically Distributed
Sensors
March 2001
Michael G. Corr and C. M. Okino
Michael designed and built a collection of small sensor
modules, each with a small processor and RF network link. When
turned on, his modules quickly identify their neighbors in the
ad-hoc wireless network and use a novel GPS-based routing
algorithm to communicate their sensor readings to a central
collection point.
 D'Agents
D'Agents
 Active Communications
Active Communications Control of Agent-Based Systems (CoABS)
Control of Agent-Based Systems (CoABS) The Automated Remote Triage and
Emergency Management Information System (ARTEMIS) is an
ongoing research effort at Dartmouth College's Institute for
Security Technology Studies that aims to provide real-time
physiological information to first responders and command
personnel in emergency/disaster situations. The prototype
system is capable of monitoring and assessing physiological
parameters of individuals, transmitting pertinent medical
data to and from multiple echelons of medical service
personnel, and providing filtered data for command and
control applications.
The Automated Remote Triage and
Emergency Management Information System (ARTEMIS) is an
ongoing research effort at Dartmouth College's Institute for
Security Technology Studies that aims to provide real-time
physiological information to first responders and command
personnel in emergency/disaster situations. The prototype
system is capable of monitoring and assessing physiological
parameters of individuals, transmitting pertinent medical
data to and from multiple echelons of medical service
personnel, and providing filtered data for command and
control applications. The system employs wireless
networking, portable computing devices, and reliable
messaging technology as a framework for information analysis,
information movement, and decision support capabilities.
Physiological status assessment is based on a medical model
that relies on input from humans and a pulse oximetry device.
Our physiological status determination methodology follows
NATO defined guidelines for remote triage and is implemented
using an approach based on fuzzy logic. The approach
described on this website can be used in both military and
civilian settings.
The system employs wireless
networking, portable computing devices, and reliable
messaging technology as a framework for information analysis,
information movement, and decision support capabilities.
Physiological status assessment is based on a medical model
that relies on input from humans and a pulse oximetry device.
Our physiological status determination methodology follows
NATO defined guidelines for remote triage and is implemented
using an approach based on fuzzy logic. The approach
described on this website can be used in both military and
civilian settings. We are interested in
developing models of both AP-association patterns and
physical user movements. The former presents how mobile users
roam from one AP to another, while the latter describes how
mobile users move in a physical space. To develop an
association model, we first extract the characteristics of
association patterns directly from the syslog messages
(available on this site). We then derive an association model
from these characteristics. To develop a physical-mobility
model, however, we first need to estimate the physical
location of users from the association patterns; this task is
not easy because a mobile device does not necessarily
associate with the geographically-closest AP. Our path
extractor estimates paths from AP-association patterns and
has been validated against GPS track data as shown in the
figure. These extracted paths are used for developing a
physical-mobility model.
We are interested in
developing models of both AP-association patterns and
physical user movements. The former presents how mobile users
roam from one AP to another, while the latter describes how
mobile users move in a physical space. To develop an
association model, we first extract the characteristics of
association patterns directly from the syslog messages
(available on this site). We then derive an association model
from these characteristics. To develop a physical-mobility
model, however, we first need to estimate the physical
location of users from the association patterns; this task is
not easy because a mobile device does not necessarily
associate with the geographically-closest AP. Our path
extractor estimates paths from AP-association patterns and
has been validated against GPS track data as shown in the
figure. These extracted paths are used for developing a
physical-mobility model.








 In pervasive computing, many
applications will be context-aware; that is, the applications
adapt their behaviors according to user's situation or
environment. We are examining the potential for making
authorization decisions (such as access to a medical
database) based on the context of the user making the
request. Such a context-sensitive authorization scheme is
necessary when mobile users (e.g., first responders) move
across multiple administrative domains where they are not
registered into the systems in advance. For example, in the
First Responder project, a granting decision could depend on
a requester's current location or medical conditions, which
is obtained from the information servers. The information
servers, in return, collect situational information from a
sensor network that covers an emergency area. Since context
information, such as the location of the user, might allow an
malicious party to infer the user's private information, we
particularly address the issue of protecting confidential
information involved in authorization policies to protect the
users' privacy.
In pervasive computing, many
applications will be context-aware; that is, the applications
adapt their behaviors according to user's situation or
environment. We are examining the potential for making
authorization decisions (such as access to a medical
database) based on the context of the user making the
request. Such a context-sensitive authorization scheme is
necessary when mobile users (e.g., first responders) move
across multiple administrative domains where they are not
registered into the systems in advance. For example, in the
First Responder project, a granting decision could depend on
a requester's current location or medical conditions, which
is obtained from the information servers. The information
servers, in return, collect situational information from a
sensor network that covers an emergency area. Since context
information, such as the location of the user, might allow an
malicious party to infer the user's private information, we
particularly address the issue of protecting confidential
information involved in authorization policies to protect the
users' privacy. We developed a secure logic-based
authorization system where authorization policies are
expressed as logical rules (i.e., Horn clauses). A request is
granted if the authorization server succeeds in constructing
a proof tree that derives the granting decision. Our
decentralized scheme does not need a universally trusted
central authorization server that maintains all the context
information; the authorization decisions are made by multiple
hosts, each of which only has partial knowledge about the
context information, in a peer-to-peer way. Our novel
distributed algorithm decomposes a proof tree into multiple
subproof trees produced by different hosts so that
confidentiality policies of each host are satisfied. We are
deploying our current implementation into an emergency
response system to evaluate the performance and scalability
of the system.
We developed a secure logic-based
authorization system where authorization policies are
expressed as logical rules (i.e., Horn clauses). A request is
granted if the authorization server succeeds in constructing
a proof tree that derives the granting decision. Our
decentralized scheme does not need a universally trusted
central authorization server that maintains all the context
information; the authorization decisions are made by multiple
hosts, each of which only has partial knowledge about the
context information, in a peer-to-peer way. Our novel
distributed algorithm decomposes a proof tree into multiple
subproof trees produced by different hosts so that
confidentiality policies of each host are satisfied. We are
deploying our current implementation into an emergency
response system to evaluate the performance and scalability
of the system.